Intro
Write-up for the Opacity TryHackMe Machine
Walkthrough
Once connected to the box I started by running an nmap scan to identify any active services on the machine
nnmap -sC -sV 10.10.132.80
sC : default scripts sV : enumerate versions
Initial Foothold
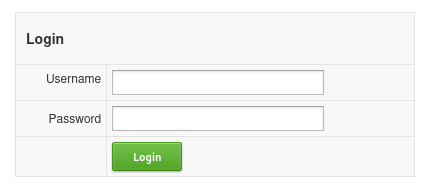
We are met with a login page.
After several attempts of manually trying default credentials I performed directory enumeration using ffuf
ffuf -w /opt/SecLists/Discovery/DNS/subdomains-top1million-20000.txt:FUZZ -u http://10.10.132.80/FUZZ
The directory enumeration returned a /cloud directory, visiting the URL presented us with a file upload
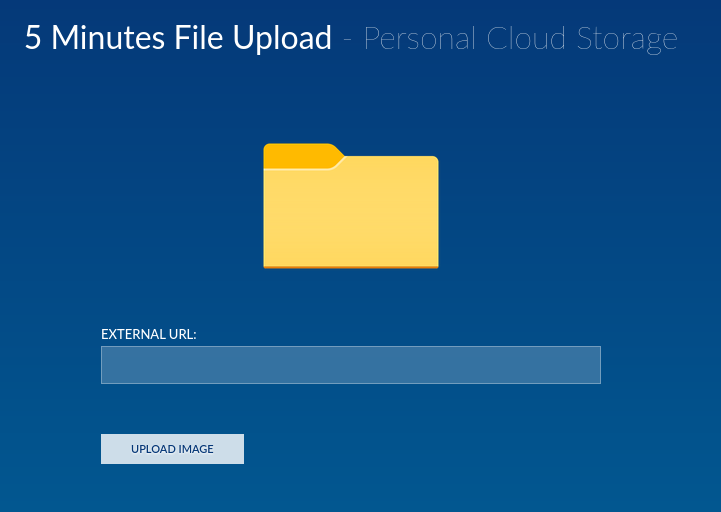
Despite the login page earlier being of no immediate value, I remeber visiting the url lead us to a login.php page. This meant that php was running on the server. This lead to me uploading a php reverse shell.
I setup a local server using python and crafted the php reverse shell using Revshells.
python3 -m http.server 80
Finally, I setup a netcat listener on the same port as the reverse shell.
nc -lvp 7777
The file upload rejected the php extension, but after trying various image extensions along with a buffer character I manged to upload the payload successfully.
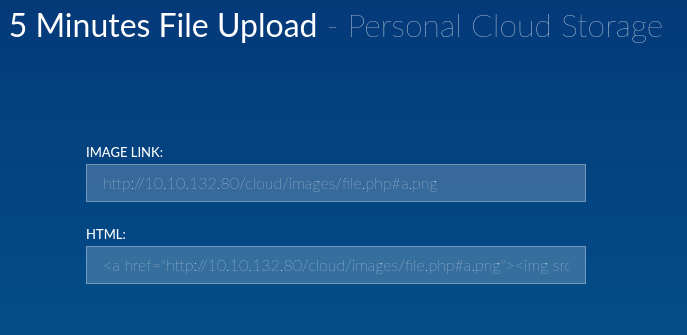
We are able to then call the URL and trigger the reverse shell
The first thing I like to do is upgrade the shell, so I check if python is on the system (not only is this beneficial in upgrading the shell, but it is also useful for setting up a server).
python -c 'import pty; pty.spawn("/bin/bash")'
Once connected to the server I browsed through the various directories until I found a specific file of interest, namely: dataset.kdbx
I then set up a server on the remote machine and obtained the file for decryption
python3 -m http.server 80
wget http://10.10.132.80:80/opt/dataset.kdbx
Utilising keepass2john I was able to make a hash of the dataset
keepass2john dataset.kdbx > dataset-hash.txt
Passing this hash into john allows us to access the password for the dataset
john --wordlist=/usr/share/wordlists/rockyou.txt dataset-hash.txt
Retrieve the password by opening dataset.kdbx in Keepass
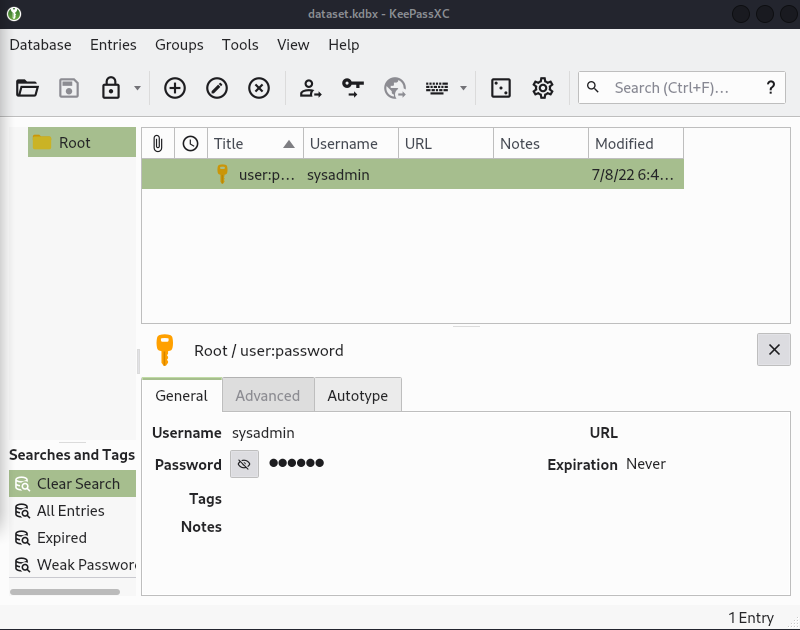
I tried enterring these login credentials into the login.php page - no luck. However, I identified a port 22 from the earlier nmap scan so attempted to SSH onto the server using the newly found credentials.
ssh sysadmin@10.10.132.80
Success - User flag obtained ✅
Privilege escalation
Browsing through the diretories, I find script.php to be particularly interesting as it makes a call to a backup php file, lib/backup.inc.php. While the sysadmin user does not have write access in that directory, I am able to create a backup.inc.php file and add our php reverse shell into the file (using the same code from earlier).
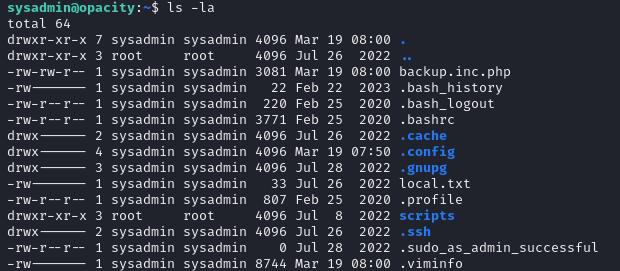 Additionally, I setup the net cat listener again
Additionally, I setup the net cat listener again
nc -lvp 7777
At this point, I was unsure how this script.php is actually called. But running htop I find the process being called by root

After a few seconds I notice the net cat listener return a shell with root access. Root flag obtained ⛳